This article was co-authored by Clinton M. Sandvick, JD, PhD. Clinton M. Sandvick worked as a civil litigator in California for over 7 years. He received his JD from the University of Wisconsin-Madison in 1998 and his PhD in American History from the University of Oregon in 2013.
The wikiHow Tech Team also followed the article's instructions and verified that they work.
This article has been viewed 78,585 times.
E-mail fraud can be dangerous. People often inadvertently give out highly sensitive information via e-mail and end up in financial, legal, or personal trouble. If you notice a fraudulent e-mail in your inbox, it's important to be vigilant and report it. You can prevent the scam from spreading further by alerting the proper authorities of its existence.
Steps
Recognizing Fraudulent E-mails
-
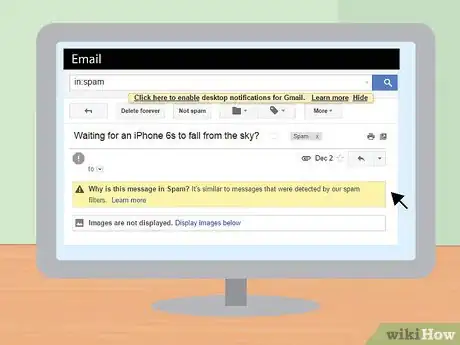
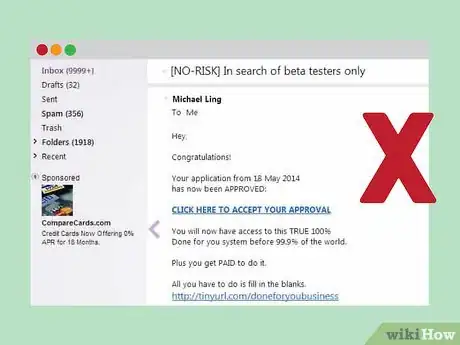
1Familiarize yourself with typical scam emails. In order to report scams, you need to be able to recognize a fraudulent e-mail. There are a variety of scam e-mails in circulation, and typical scams e-mails include the following.
- Traditional scams usually come in the form of some bogus offer. It's often a business offer that claims you can make a large sum of money each month online. It can sometimes be a health and fitness offer, boasting natural remedies of new foods or exercises that can help you shed unreasonable amounts of weight or inches in short periods of time. Usually, the scam is an attempt to fool the recipient into giving out personal information online.[1]
- Sometimes scam e-mails will offer discount software that, if downloaded, contains malware, viruses, and other malicious software designed to get personal information off your computer.[2]
- Certain frauds, referred to as 419 frauds, work by enticing a victim with a series of phony documents and claims, usually regarding large sums of money or legal violations. These e-mails might claim you are next of kin to a wealthy Nigerian business owner, for example, or accuse you of violating the Patriot Act and then demand you pay some kind of fine. The goal of such frauds is to get as much money and information as possible from you. Once the scammer feels he's gotten all he can, he'll cease communication.[3]
- Traditional scam e-mails can usually be spotted by common sense alone. The old adage "If it sounds too good to be true, it probably is" is a good measure of a scam e-mail. Conversely, if it seems too bad to be true this is also probably the case. You likely cannot lose 20 pounds in one week using newly discovered berries from the Amazon rainforest. You also probably did not violate the Patriot Act by sharing a news article on Facebook.[4]
-
2Be aware of phishing scams. Phishing scams are a newer form of scam e-mail. In a phishing scam, the scammer imitates a legitimate website to trick you into logging on to a phony version of a well-known site like Facebook or Twitter. The goal is to either get you to inadvertently download malware or to give out sensitive personal information.[5]
- Usually, a phishing e-mail will appear to be a legitimate e-mail from your bank or a social media website like Facebook. It will have an urgent subject line like "Problem with Your Bank/Account" and the content will demand you validate your account by filling out an online form. When you click the link provided, the site will look remarkably similar to the real website. This is why phishing scams are so dangerous. They're often successful.[6]
- You should regard any e-mail asking for personal information over the internet with skepticism. Call your bank to verify the legitimacy of any e-mail you receive, and google the subject line if the e-mail's from a social media site. Chances are, your google search results will identify the subject line as part of a recent scam.[7]
- There is also a website, known as the Anti-Phishing Workshop Group, that keeps and up-to-date catalogue of various phishing scams. Look through their listings if you receive any suspicious e-mails you suspect are phishing scams.[8]
Advertisement -
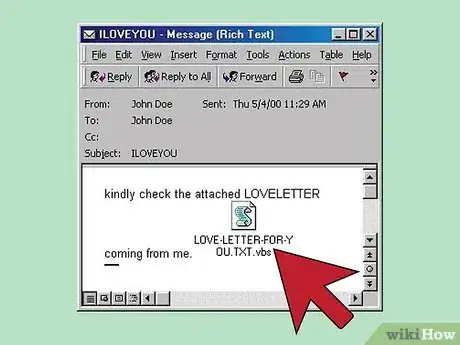
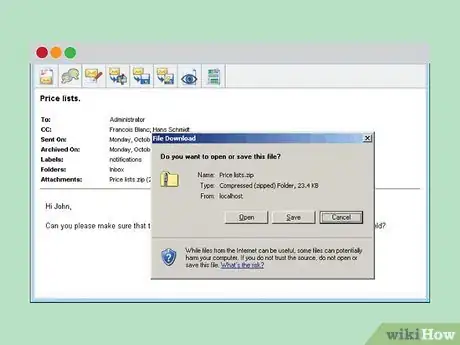
3Watch out for Trojan Horse e-mails. Trojan Horse e-mails usually operate by offering some kind of service via download, only to release viruses onto your computer.
- Oftentimes, Trojan e-mails will have a strange subject line and then ask recipients to open an attachment. For example, the popular "Love Bug" virus arrived with the subject line "I Love You" and then asked users to open an attachment to receive a love letter, resulting in their computer being infected with a virus.[9]
- Trojan e-mails may also pose as a virtual postcard, promise a funny joke in an attachment, or offer to install a virus sweeper for free. In general, do not open attachments from senders you do not recognize.[10]
Reporting Scams on Different E-mail Accounts
-
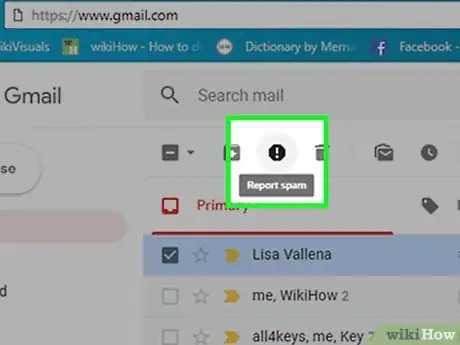
1Report scams on your Gmail address. If you use Gmail, the means to report a scam is fairly straight forward.
- Log into your Gmail account.
- Select the email that you want to report.
- You can do this either by opening the email or by selecting the check mark next to it.
- Click on the Spam button. It looks like a Stop sign with an exclamation point in it.
-
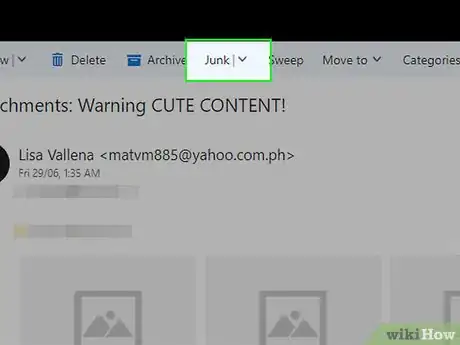
2Tell Outlook.com about spam. Outlook.com (formerly known as Hotmail) has a very simple means of dealing with scam e-mails. You simply click on the Junk button, which is near the top.
- Simply select the email that you want to report, then click on Junk.
- A drop down menu may come up, if it does, then select the appropriate category to report the email as.
- Simply select the email that you want to report, then click on Junk.
-
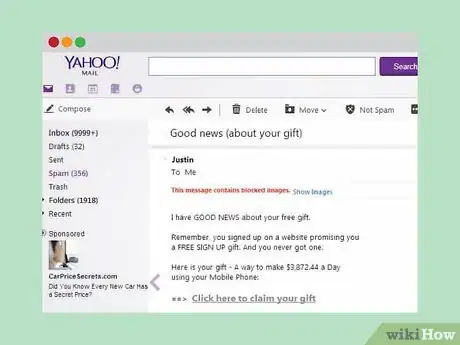
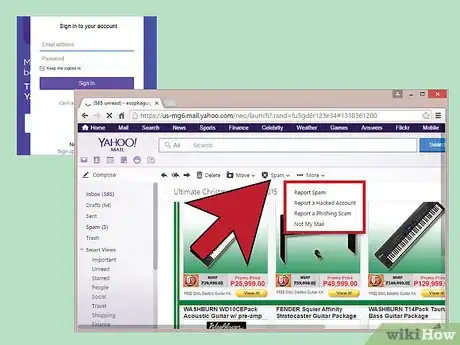
3Report scam e-mails on Yahoo. For Yahoo, you'll need to go through Yahoo's website to report fraudulent e-mails.
- Log onto your Yahoo account and click "Yahoo Account" on the top of the page. From there, click "abuse and spam."[11]
- Yahoo will offer a variety of categories to choose from, such as "Report phishing" and "Received spam e-mail or IM message."
- Select the category that is most relevant. You will be redirected to a form asking for basic information, such as your e-mail address, the address of the suspicious e-mail, and details about its contents, subject line, and header. Fill out this information to the best of your ability.
-
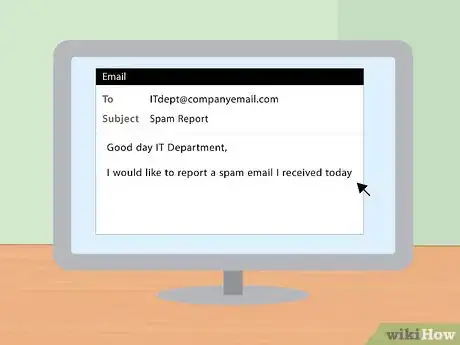
4Report scam e-mails to the IT department if you receive them on a work or school computer. If you're receiving scam e-mails on an e-mail address you use for work or school, report them to the IT department in addition to reporting them through the e-mail server itself. The IT department will know how to handle phishing scams and other frauds and should be able to identify the culprits. It's also possible your work or school is being specifically targeted by scammers. You should make sure that information is widely known to prevent people from falling victim to a scam.
-
5Understand where you can report general complaints. It's a good idea to report fraudulent e-mails to the general public and any law enforcement agencies that could help identify and stop the scammer. In addition to reporting a fraudulent e-mail to your e-mail provider, try the following routes.
- Emailbusters.org will publicize frauds in order to make people aware of what messages to avoid or delete.[12]
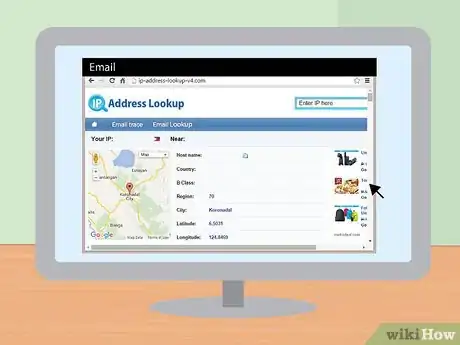
- Ip-Address-Lookup-V4 is a site that can find the sender's e-mail and IP address. This can help identify scammers.[13]
- If the fraudulent e-mail is asking for banking or other personal information, you should report it to the FBI's Complaint Center. The proper authorities can find and penalize scammers. This minimizes the number of victims of fraud.[14]
Avoiding Fraud in the Future
-
1Use a spam filter system. One of the easiest ways to avoid fraud is to use a spam filter system in your e-mail. This means fraudulent e-mails will not go to your main inbox but will instead be redirected to a spam folder and eventually deleted.
- The majority of e-mail applications and web mail services provide the option to filter spam. If you're unsure how to add a spam filter to your email, look through the "Help" or "FAQ" on the website or application.[15]
- Some spam will still get through, even with the best filters. Do not assume, just because you have a spam filter, all your e-mails are safe. Remember how to spot phishing scams and other fraudulent e-mails.[16]
-
2Be suspicious of unsolicited e-mails. If you receive an e-mail from an individual or organization you are not familiar with, do not open it and certainly do not click any links or open any attachments provided. If you receive an e-mail that appears to be from an organization you are familiar with, do not open it if you did not request information from that organization or recently make an order, fill out a survey, or contact the organization in some way.[17]
-
3Only open attachments you trust. Attachments are one of the easiest routes for viruses and malicious software to be uploaded on your computer. Be very careful about opening attachments.
- In general, only open attachments from people you know. If you work in a field, such as publishing, where you may receive e-mail attachments from strangers make sure the e-mails are legitimate. Phony e-mails can be spotted by heavy grammatical errors, as they're often produced via a spambot and not a person.[18]
-
4Install and regularly update antivirus software. Antivirus software is a powerful means of protecting yourself from fraud.
- If possible, find an antivirus software that updates on its own. Oftentimes, people accidentally forget to update so having automatic updates might better protect you against e-mail and fraud.[19]
- Make sure any antivirus software you use has an email scanning system in place. This can help you avoid downloading attachments that contain viruses.[20]
-
5Learn the e-mail policies of companies you work with. The best protection against a scam is education. Know the policies of the companies you work with in regards to e-mail so you can better recognize phishing scams.
- Most commercial banks have a strict policy against asking for personal information via e-mail. You're more likely to receive a phone call to confirm suspicious charges than an e-mail. If you receive an e-mail asking for personal information, phone your bank to confirm before filling out any online forms.[21]
- Social media sites, like Facebook and Twitter, all have e-mail policies regarding your account's security. Familiarize yourself with these policies and know when and why an e-mail from Twitter or Facebook might be appropriate.[22]
References
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ http://ip-address-lookup-v4.com/article/reportemails.php
- ↑ http://ip-address-lookup-v4.com/article/reportemails.php
- ↑ http://ip-address-lookup-v4.com/article/reportemails.php
- ↑ http://ip-address-lookup-v4.com/article/reportemails.php
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
- ↑ https://www.us-cert.gov/sites/default/files/publications/emailscams_0905.pdf
About This Article
To report scam e-mails to your Gmail account, click the checkbox next to the e-mail you want to report and click the "Spam" button, which looks like a stop sign with an exclamation point inside it. If you're using Outlook, select the e-mail you want to report and click the "Junk" button at the top of the page. You can use your main account page to report scam e-mails to your Yahoo email by clicking "Abuse and Spam." If you're receiving scam mail on an e-mail address you use for work or school, report it to the IT department after you report it to the e-mail server. For tips on recognizing different kinds of fraudulent e-mails, read on!